|  |
Appendix A. IP Packet Routing
Routers and gateways join multiple IP networks, forwarding packets between the networks. A single organization may have multiple IP networks because it has multiple buildings, multiple sites, or multiple subgroups that require their own networks. For example, the history and math departments at a university are likely to each have their own IP networks, just as an engineering and manufacturing facility separated by several miles will have independent networks. Section 17.2, "Network partitioning hardware" discussed network partitioning using routers, and some of the performance considerations when running NFS and NIS in an internetworked environment. This appendix explores the mechanics of IP packet routing in greater detail.
A.1. Routers and their routing tables
A router has a unique IP address on each network interface; associated with each IP address is also a unique hostname. A common convention is to add a suffix associated with the network number to the name of the host used on the each network interface as shown in this /etc/hosts fragment:[60][60]Of course, identifying a host's interfaces in /etc/hosts is not sufficient if you are using DNS. An excellent treatment of how to set up multiple interfaces for a host in DNS is discussed on the Web in the document "Frequently Asked Questions about Kerberos" by Ken Hornstein, available (at the time this book was written) at http://www.nrl.navy.mil/CCS/people/kenh/kerberos-faq.html. Look for the section entitled "How should I configure my DNS for Kerberos?" Even if you are not using Kerberos, Hornstein's recommendation for "multiple address records per host" is a logical way to configure multiple interfaces in DNS, because his choice associates a single name, such as fred.widget.com, with multiple interface specific names, such as fred-200.widget.com and fred-201.widget.com.
Host fred is on both the 192.9.200.0 and 192.9.201.0 networks, and has a distinct name and address on each. netstat -i shows both interfaces and their associated networks and hostnames:# # local network hosts # 192.9.200.1 fred fred-200 192.9.200.2 barney 192.9.200.3 wilma # # remote network gateway 192.9.201.1 fred-201
To send a packet to another network, the local host needs some picture of the network and its connections to other networks. Ideally, this picture presents other networks as a "black box" outside of some local gateway, rather than an itemization of a route to every host on every attached network. This paradigm is how we view the U.S. Post Office. Once you drop a letter in the mailbox, the route it takes may involve trucks, planes, or people, and the decisions about routing vehicles are left up to the people doing the delivery.% netstat -i Name Mtu Net/Dest Address Ipkts Ierrs Opkts Oerrs Collis Queue hem0 1500 192.9.200.0 fred 349175 104 542039 363 816 0 hme1 1500 192.9.201.0 fred-201 108635 1 4020 22 301 0 lo0 8232 loopback localhost 74347 0 74347 0 0 0
A host's picture of the local network's connections to other IP networks is contained in the kernel's routing table. This table may be modified in three ways:
-
Dynamic routing information is
sent periodically by routers that
advertise themselves using some well-known protocols, and daemons
such as in.routed send and interpret route
announcements and update the routing table.[61]
[61]The protocol used by in.routed is called RIP, for Routing Information Protocol. There are other routing protocols that send less information or that allow hosts to perform preferential routing when multiple gateways are present, but a discussion of these protocols is beyond the scope of this book.
-
Static routing involves hand-crafting
a route table. Static routing is
typically used when there is only one router on a network, so a
single route suffices for all outbound traffic. Client machines often
set up static routing to avoid having to listen to the regular route
information broadcasts (see Section A.2, "Static routing" later
in this appendix).
-
Route redirection requests are
sent by routers that are asked to
forward packets to networks for which the chosen router is not the
best choice. These route table updates are sent in
ICMP redirect
messages.
The term "gateway" is used somewhat improperly in both netstat -r and the following discussion. A gateway performs services at the application layer in the protocol stack, while a router is concerned only with the IP layer. The routing tables show IP routes, and titling the Gateway column Router instead would be more correct. However, many people associate Router with a dedicated IP router, so the less specific term Gateway is used.% netstat -r Routing tables Destination Gateway Flags Refcnt Use Interface 131.40.191.1 gatehost UGH 0 0 hme0 131.40.56.0 gatehost UG 0 0 hme0 131.40.208.0 gatehost2 UGD 0 0 hme0 131.40.52.0 wahoo U 60 80770 hme0 localhost localhost UH 4 4767 lo0 default gatehost UG 0 0 hme0
The information in the routing table determines how to get to a particular remote host or network, and shows the usage statistics for each route. The destination column shows the remote address; if it is a remote network, the address has a .0 suffix to indicate that it is a network number.[62] Note that you can get to multiple networks through a single gateway. The gateway listed in the routing tables is just the first step that must be taken to reach the remote network; additional routing information on the first gateway directs a packet to another gateway if required.
[62]Of course, if you are using classless IP addressing (see Section 1.3.4, "Classless IP addressing"), network numbers are likely to not fall in discrete 8-bit widths. Thus in a classless environment, it would be more precise to say that if the destination is a remote network, the last N bits of the address will be zeroes to indicate that the first 32 - N bits of the address are a network number.The Flags column describes the gateway:
- U
-
The gateway is up. If this flag appears in netstat
-r, the gateway is probably up.
- G
-
To get to the destination address, packets must go through a gateway.
The gateway's name is in the second column.
- H
-
The gateway is a "host gateway" and is directly connected
to the network listed as the destination. In the first line of the
routing table in the previous example, destination 131.40.191.1 is
the IP address of gatehost, the gateway
referenced in several other route table entries. Host gateways are
always listed with their full IP addresses as the destination and are
generally at the far end of a point-to-point link.
- D
-
The route was added after receiving an ICMP redirect message. The
local host probably sent a packet to some other router, such as
gatehost, with a destination network of
131.40.208.0. gatehost consulted its routing
tables and found that the router to this network was
gatehost2, and to get to
gatehost2 it had to send the packet back out on
the same network interface on which it was received. The IP routing
algorithm realizes that it should never have been handed a packet for
this network in the first place, so it sends an ICMP redirect message
to the originator informing it of a better route to network
131.40.208.0. Using static routes in a network with multiple gateways
can lead to a steady stream of ICMP redirect requests unless the
transmitting hosts update their route tables. Figure A-1 shows the generation of an ICMP redirect
message.
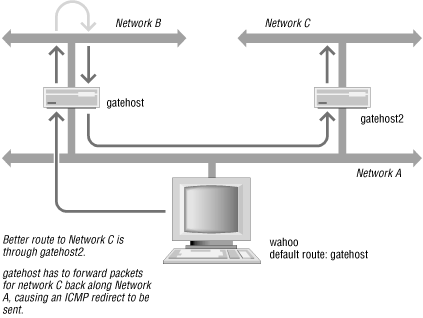
Figure A-1. ICMP redirect generation
The last column in the output of netstat -r shows the physical or pseudo device used to reach the gateway. The last three routes deserve some additional explanation. The route with wahoo as the gateway describes the local host's connection to the local network. This is known as the interface route of the machine. The next entry shows the loopback device, which is listed as a host gateway. The last line is a default routing entry, which is used as a catchall if the destination IP network cannot be matched to any explicit route in the table.The combination of the flags U, G, and H implies "This host is the gateway to this network": the U flag means the gateway is up, the G flag means the packets must go through a gateway, and the H flag indicates that the remote network is connected to the host listed in the route table. The gateway host has at least one network interface and one or more point-to-point links. A gateway listed with flags U and G has two or more network interfaces and is acting as a routing host. The lack of the H flag means that the remote network isn't attached directly to the gateway; the gateway host listed in the routing table is merely a stepping stone on the way to that remote network.
Armed with the route tables, we can locate the host on our local network that can forward our packets to any destination host. Since we need the MAC address of the destination to send a packet, this presents a problem for the transmitter when the receiver is on another network. How do packets actually get to the remote network?
Let's assume that wahoo, at IP address 131.40.52.15, has mounted a filesystem through one or more gateways from the NFS server bigguy at IP address 131.40.208.10. To send a packet to bigguy, wahoo looks for its IP address in its routing table. It finds it, with gatehost2 named as the gateway to this network. If the remote IP network was not matched to a destination in the routing tables, the default route, which uses gatehost, would be used. wahoo sends its packet to gatehost2, filling in the MAC address for gatehost2 but the IP address for bigguy.
When gatehost2 receives the packet, it realizes that the IP network in the destination field is not its own. It forwards the packet, using its own routing information to locate a gateway to network 131.40.208.0. gatehost2 sends the packet to the next gateway, putting in the remote gateway's MAC address but leaving the destination IP address of bigguy intact. Eventually, the packet is received by a gateway that is on network 131.40.208.0; this gateway recognizes that its IP network and the destination IP network in the packet are the same, and it sends it along the local area network to bigguy. The last gateway to forward the packet is the one that inserts bigguy's MAC address in the packet.
By default, hosts on more than one network are configured as routers in order to forward packets from one interface to another. In some cases, it's desirable to disable automatic IP forwarding, so that the host may communicate on multiple networks but it will not act as a transparent conduit between them. Refer back to the NIS security issues raised in Section 12.3.2, "Making NIS more secure". If an NIS client can bind to an NIS server, it can dump the password map from the server. To protect the contents of your password file map, you may want to make it impossible for clients outside the local network to bind to a local NIS server. With IP forwarding enabled, any client can use ypset to get to any NIS server, but if IP forwarding is disabled on the host that connects the local network to other networks, ypset never makes it beyond this router host. It's also a good idea to disable IP forwarding on machines that join your company network to a larger network such as the Internet. This creates a firewall between your internal networks and the outside world: hosts outside the router cannot get packets into your company networks.
How you disable IP forwarding depends on your system. In Solaris, this is done by creating a special file:
If the /etc/notrouter file is present when the system boots, then the system will not perform IP forwarding. If you want to turn off IP forwarding immediately, then do the following:# touch /etc/notrouter
# /usr/sbin/ndd -set /dev/ip ip_forwarding 0