|  |
6.2. Screened Host Architectures
Whereas a dual-homed host architecture provides services from a host that's attached to multiple networks (but has routing turned off), a screened host architecture provides services from a host that's attached to only the internal network, using a separate router. In this architecture, the primary security is provided by packet filtering. (For example, packet filtering is what prevents people from going around proxy servers to make direct connections.)Figure 6-3 shows a simple version of a screened host architecture. The bastion host sits on the internal network. The packet filtering on the screening router is set up in such a way that the bastion host is the only system on the internal network that hosts on the Internet can open connections to (for example, to deliver incoming email). Even then, only certain types of connections are allowed. Any external system trying to access internal systems or services will have to connect to this host. The bastion host thus needs to maintain a high level of host security.
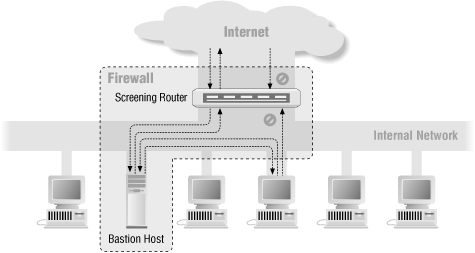
Figure 6-3. Screened host architecture
Packet filtering also permits the bastion host to open allowable connections (what is "allowable" will be determined by your site's particular security policy) to the outside world. The Section 6.3.2, "Bastion Host" in the Section 6.3, "Screened Subnet Architectures" discussion, later in this chapter, contains more information about the functions of bastion hosts, and Chapter 10, "Bastion Hosts", describes in detail how to build one.The packet filtering configuration in the screening router may do one of the following:
- Allow other internal hosts to open connections to hosts on the Internet for certain services (allowing those services via packet filtering, as discussed in Chapter 8, "Packet Filtering")
- Disallow all connections from internal hosts (forcing those hosts to use proxy services via the bastion host, as discussed in Chapter 9, "Proxy Systems")
Because this architecture allows packets to move from the Internet to the internal networks, it may seem more risky than a dual-homed host architecture, which is designed so that no external packet can reach the internal network. In practice, however, the dual-homed host architecture is also prone to failures that let packets actually cross from the external network to the internal network. (Because this type of failure is completely unexpected, there are unlikely to be protections against attacks of this kind.) Furthermore, it's easier to defend a router than it is to defend a host. For most purposes, the screened host architecture provides both better security and better usability than the dual-homed host architecture.
Compared to other architectures, however, such as the screened subnet architecture, there are some disadvantages to the screened host architecture. The major one is that if an attacker manages to break in to the bastion host, nothing is left in the way of network security between the bastion host and the rest of the internal hosts. The router also presents a single point of failure; if the router is compromised, the entire network is available to an attacker. For this reason, the screened subnet architecture, discussed next, has become increasingly popular.
Because the bastion host is a single point of failure, it is inappropriate to run high-risk services like web servers on it. You need to provide the same level of protection to it that you would provide to a dual-homed host that was the sole firewall for your site.
6.2.1. Appropriate Uses
A screened host architecture is appropriate when:
- Few connections are coming from the Internet (in particular, it is not an appropriate architecture if the screened host is a public web server).
- The network being protected has a relatively high level of host security.